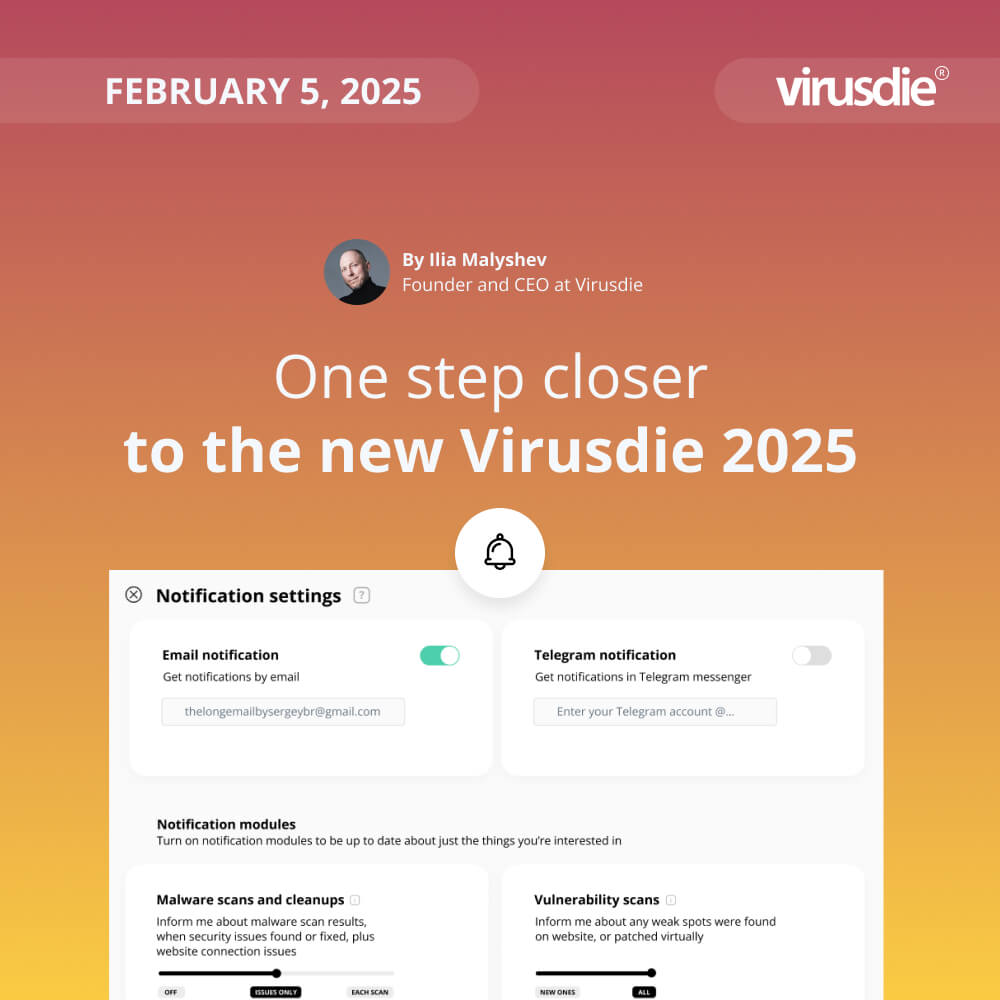
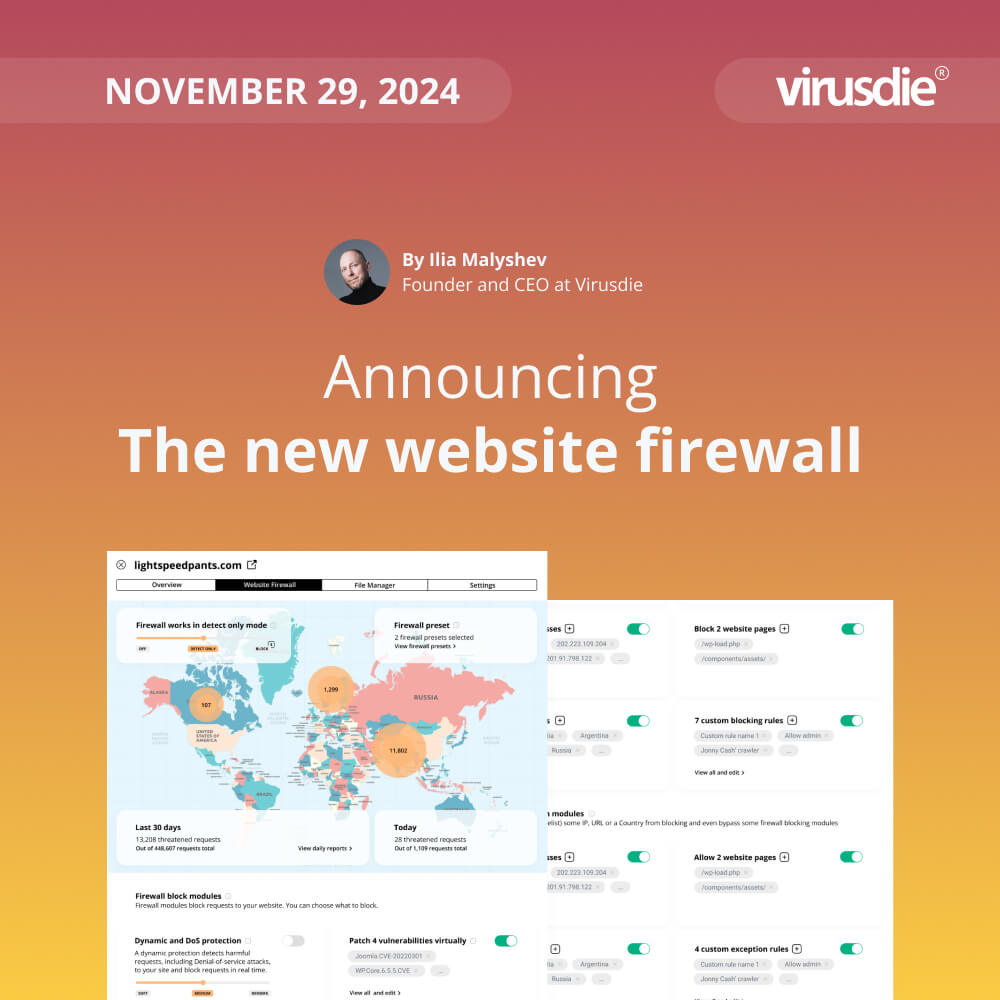
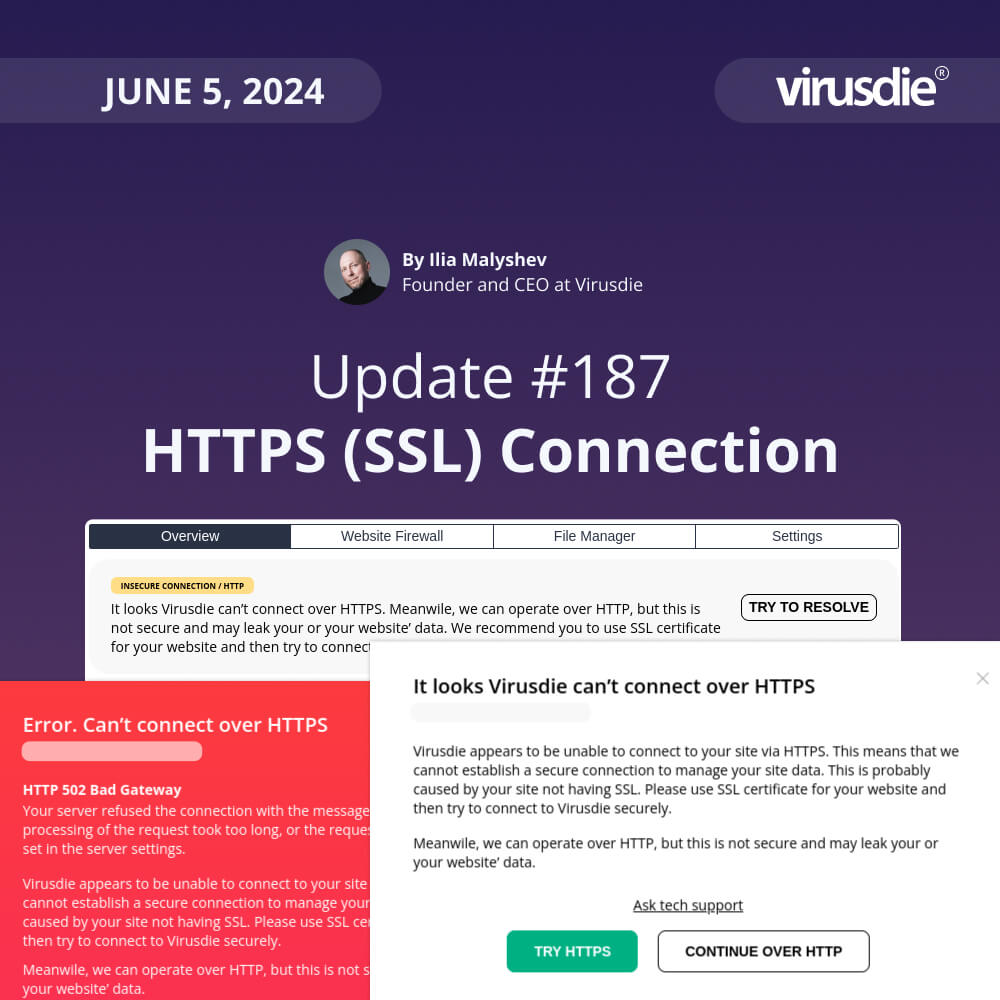
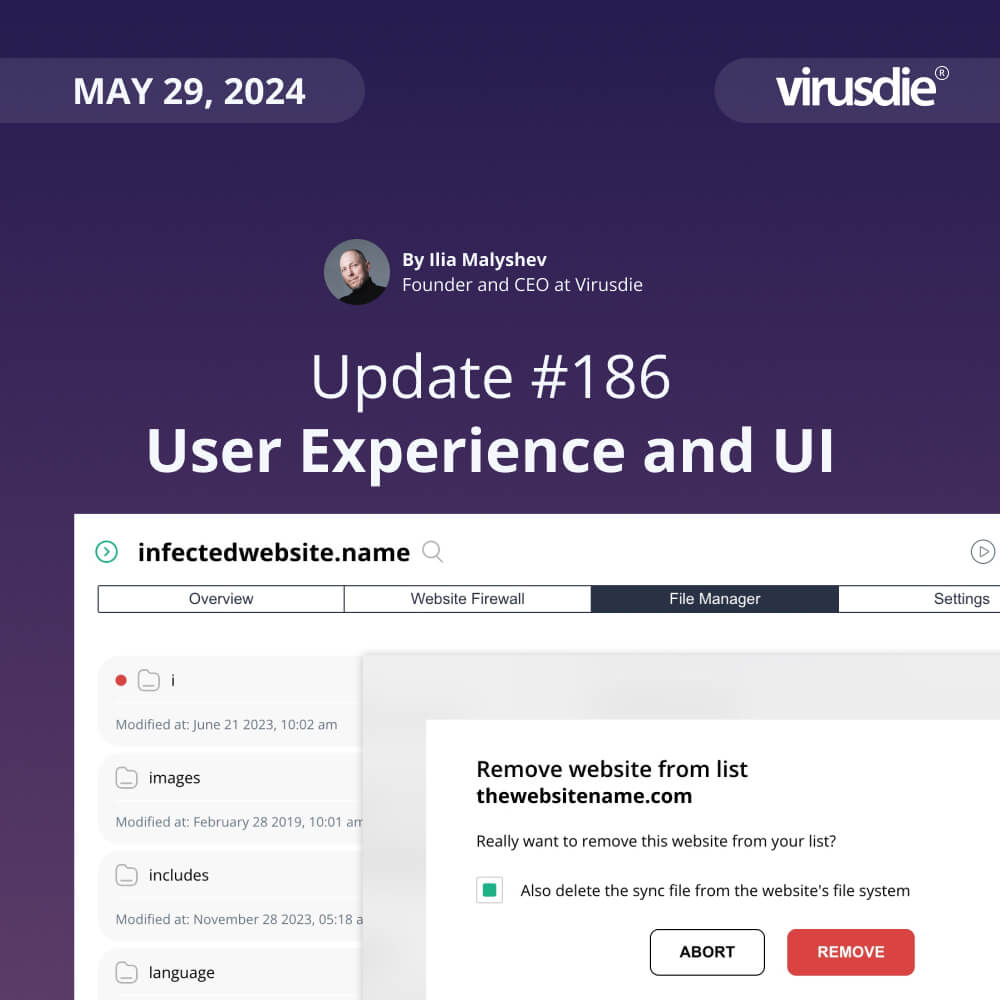
JUNE 5, 2024 | Weekly Update 187: Alerts and recommendation about your site’ insecure connection to Virusdie over HTTP (instead HTTPS / SSL)
This is the weekly update with a pack of new features or improvements, we try to release on weekly basis. This week it is about your Website-to-Virusdie connection security. Now we alert you if you connect over HTTP insecurely.
Alerts about insecure connection over HTTP
Virusdie is all about security. And the service operation should be secure as well, of course. The way Virusdie connects your sites is HTTP / HTTPS protocol, to manage your website security. And Virusdie always check if you have an SSL certificate for your domain and tries to connect over secure connection – HTTPS.
And that all looks pretty well. However, we found, that for some server setups and your website/host settings, that could be incorrect HTTP – HTTPS redirect rules for your domain. And that means, that Virusdie can’t connect over HTTPS for such cases.
Previously, Virusdie tried to switch to HTTP protocol for that cases, to try to connect to your website. And it runs well if it can. The problem was the thing – we do not alert you about insecure connection. So you can’t feel the problem.
Now that fixed! Now we alert you with all the details and recommended actions to take, if Virusdie can’t connect to your site over secure HTTP (SSL) protocol. And you can view all these alerts across your dashboard – at the list of websites, at top side of any sidebar tab, and at alert modal windows as well.
So now, your website connection security is always under your fingertips!
Hope, you found this update helpful 🙂
Ilia Malyshev,
Founder and CEO at Virusdie.
——
Join our private Facebook group to get help from other security experts, and share your own web security experiences and expertise. Group members receive exclusive news and offers. They can also communicate directly with the Virusdie team. Join us on Facebook.
Website: https://virusdie.com
Virusdie roadmap: https://virusdie.com/company/roadmap/
YouTube: Virusdie Channel
Facebook: WebSecCommunityVirusdie
Twitter: https://twitter.com/VirusdieCloud
Instagram: https://www.instagram.com/virusdiecloud/