IMPROVE YOUR SKILLS | How to deal with and how Virusdie can help with the new SEO Spam Campaign That Changes WordPress Core Files and Database
That looks it is time to learn something new and important. Daria, the head of Anti-malware database (BASE) at Virusdie is going to improve your skills and share some details about the dangerous SEO-spam campaign against WordPress websites. That campaign been recently discovered and processed by Virusdie BASE team so, that is fair to share some knowledge with you, right? 🙂
We have recently detected a wave of unusual SEO spam infections. SEO spam is a kind of malware that substitutes data on someone’s website for search engines to promote third-party sites. For instance, if your site is a medical blog, but it is infected with this kind of virus, then for search engines, it will look like this:
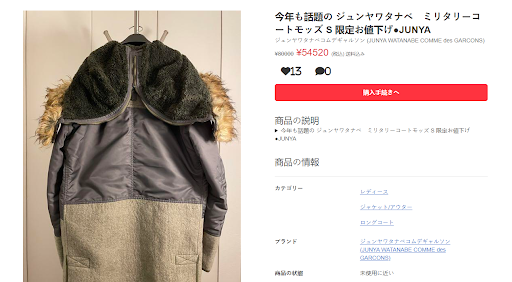
This attack does not have a specific priority for websites: such a virus can trigger both small blogs as well as large online stores.
How to check quickly if you have this virus?
Have a look at the site root directory: your files index.php and .htaccess are most likely to be changed.
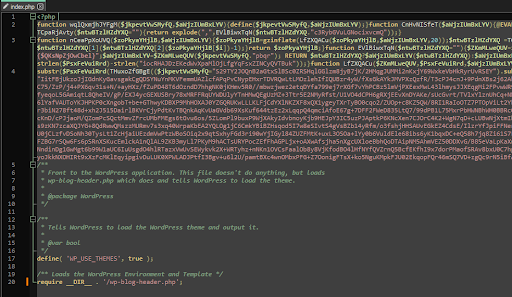
> index.php contains the main code that makes your web-platform show SEO spam instead of the relevant content of your website:
> .htaccess contains additional directives that help these scripts work more efficiently.
> atom.php is a temporary file of that infectious campaign.
If you try to bring index.php and .htaccess to the standard view, they will instantly be overwritten by the virus. Why is this happening?
Let’s take a closer look
This malware changes the following WordPress core files, adding suspicious functions to them:
> wp-includes/blocks/navigation.php
> wp-includes/comment.php
> wp-includes/option.php
> wp-includes/link-template.php
> wp-includes/taxonomy.php
All of these files contain three malware functions called wp_distribute_cp, wp_recovery_hfm, and wp_import_hfm.
The specialisation of these functions is that they connect to the site’s database, then take its data from there, which is stored in Base64 encoded text. After that, the content retrieved from the database is written into scripts, including an index file.
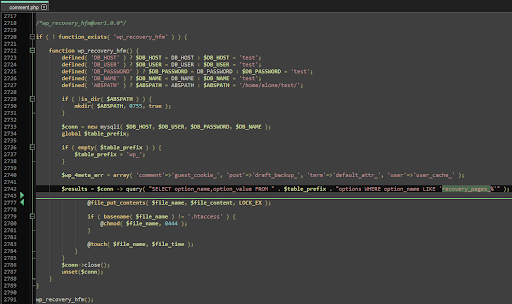
The Malware data is stored in native table options in the database. Malicious options named, e.g, “recovery_page_base64_text”:
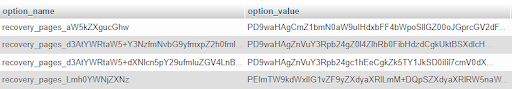
To solve the issue, you need to follow the next steps:
1. At first, you need to clean these files from extraneous functions (wp_distribute_cp, wp_recovery_hfm, wp_import_hfm) or replace them with standard WordPress files:
wp-includes/blocks/navigation.php
wp-includes/comment.php
wp-includes/option.php
wp-includes/link-template.php
wp-includes/taxonomy.php
2. Then, you may clean index.php and .htaccess. If you have completed step 1, the malicious code will not return to those files.
3. Delete additional files:
atom.php
wp-admin/css/color/light/index.php
wp-admin/user/icon/index.php
4. Delete malicious rows from the options table in the database.
5. Check your site to find possible hidden backdoors that could have been left by an attacker.
6. Update the WordPress CMS and its plugins and themes.
7. Change passwords for the WordPress admin panel, database, FTP, and hosting panel.
And of course, if you need any help in removing malware, you can use Virusdie, which will automatically and gently remove suspicious injections and backdoors for you.
By Daria Golikova,
Head of Anti-malware database (BASE) at Virusdie.
Try Virusdie 2022 pre-beta now
How to try Virusdie 2022 pre-beta? It is simple — just click on big yellow button “TRY BETA” on top of your Virusdie dashboard! 🙂
——
Join our private Facebook group to get help from other security experts, and share your own web security experiences and expertise. Group members receive exclusive news and offers. They can also communicate directly with the Virusdie team. Join us on Facebook.

Comments